This Halloween, we’re looking in depth into cyber spookiness from zombie bots to phantom phishing in the Microsoft Digital Defense Report 2024. The Microsoft Digital Defense Report addresses key insights and trends in cybersecurity that affects individuals, organizations and even nation-states. This report collected data from Microsoft’s public cloud services, Microsoft’s software and services, and telemetry from the Defense ecosystem.

Introduction: The Current State of Cybersecurity
In today’s digital world, cyber threats have evolved into a vast and multifaceted challenge impacting organizations of all industries and even nation-states. 600 million identity attacks occur per day. In the past year alone, 389 healthcare institutions in the U.S. were successfully targeted by ransomware attacks, leading to network closures, delayed medical operations, and rescheduled appointments. Just in May 2024, 176,000 incidents across 5,600 organizations have been detected by Microsoft attempting to intrude security settings.
Key Takeaways
Here are the 4 key takeaways from the Microsoft Digital Defense Report 2024:
- Diverse Motivations for Cybercrime: Threat actors are motivated by various factors, including financial gain, highlighting the need for enhanced collaboration between technological and governmental efforts to combat these threats.
- Rising Fraud Risks: Fraud is escalating, with over $1 trillion stolen globally in 2023. The rise of cloud computing has made it easier for malicious actors to launch attacks.
- Security for Organizations Against Attacks: Organizations must take a dynamic approach to data security, focusing on understanding data movement and employing integrated tools to protect sensitive information from potential leaks and oversharing.
- Leveraging AI for Cyber Defense: The integration of AI into cybersecurity is crucial for enhancing threat detection and response capabilities. Proactive strategies, including monitoring data flows and understanding attack paths, are essential for staying ahead of sophisticated cybercriminals.
Diverse Motivations for Cybercrime
Threat actors’ motivations now range from cryptocurrency theft and data destruction to ransomware and espionage. This demonstrates the variety of tactics and goals of threat actors and highlights how critical infrastructure is increasingly targeted. Since late 2023, there’s been a notable increase in attacks on operational technology (OT) systems that control vital processes like energy grids and water supplies.
To effectively deter the most advanced threats, organizations need a collaboration between technological innovation and geopolitical solutions. Companies can innovate in cybersecurity to deny cyberattacks, while governments should enforce international laws with significant consequences to deter cyberattacks. Collaboration between governments and businesses is essential, particularly when it comes to protecting critical infrastructure, including AI and intellectual property.
Rising Fraud Risks


Fraud has become prevalent in recent years. According to the World Economic Forum, over $1 trillion was stolen from victims globally in 2023. Meanwhile, the rise of cloud computing, though offering scalability and innovation, also provides malicious actors the same benefits. Fraudsters use cloud platforms to launch attacks, steal data, impersonate users, and evade detection. In fact, 775 million emails were found to contain malware in a single year.
By 2028, e-commerce payment fraud is expected to exceed $90 billion annually. Large-scale data breaches remain rampant, enabling criminals to access personal data and bypass security measures. Businesses must prioritize fraud detection and prevention strategies to address this escalating issue.
There are several ways to mitigate fraud:
- Integrate AI and machine learning models into current policies to identify unusual transaction patterns and flag potential fraud in real-time.
- Regularly scan for Shadow IT and address these unauthorized installations
- Implement risk-based containment strategies, including tiered product access and monitoring customer behavior, to counteract malicious AI usage and fake identities.
- Block known malicious domains by creating a blocklist based on domain architectures, such as IP, Whois, and information from telemetry logs often used in techscam operations.
- Maintain account security to the latest standards to prevent account takeover risks.
- Strengthen authentication methods with phishing-resistant MFA techniques.
Security for Organizations Against Attacks
Data security is no longer just about protecting data—it’s about understanding how that data moves and interacts with users, customers, and partners. With different people requiring varying levels of access, organizations need a dynamic, integrated approach to data security that balances protection and productivity. An effective data security strategy involves the classification, labeling, and protection of sensitive data across cloud and hybrid environments. Automated and integrated data security tools are essential for preventing breaches, as organizations managing over 15 tools have seen nearly three times more incidents. It’s essential not only to secure data but also to understand how it moves within the organization, who interacts with it, and the acceptable level of risk.
One of the biggest vulnerabilities companies face today is unaddressed technical debt—outdated security controls and shadow IT that leaves systems open to attack. Outdated infrastructure, unpatched systems, and abandoned applications can open security holes for cybercriminals. This issue underscores the need for organizations to modernize their security operations and establish governance over all IT assets. Organizations should also invest in AI-enabled threat detection, which can streamline cybersecurity efforts and reduce human workload.
Here are 4 ways to prepare to protect and govern data using generative AI:
- Prepare your data for generative AI by labeling it, implementing controls, and educating users on data protection.
- Limit access to sensitive files and use tools to monitor AI usage for better protection controls.
- Enhance productivity with generative AI by optimizing data governance and loss prevention and leveraging advanced risk management capabilities.
- Use generative AI to drive innovation by expanding its adoption across the organization, improving user accountability, and extending data governance.
Preparing Generative AI for Data Security
When generative AI apps are deployed on ungoverned data estates, they can lead to data leaks or oversharing since users may access sensitive information. Studies show that 83% of organizations have experienced multiple data breaches. To prevent this, data environments must be prepared for AI by inventorying data, identifying sensitive information, and labeling and protecting it. Applying data loss prevention policies for both the input and output of AI apps can help stop overexposure and leaks.
AI helps data security teams enhance loss prevention, classification, and encryption. It identifies data boundaries, improves governance, and suggests policy improvements. Generative AI handles large data sets, making security management more efficient.
Impacts on Operational Technology
Threat actors are targeting operational technology (OT) devices to access critical networks, move laterally within systems, and disrupt operations. To enhance security in this sector, the industry should take three key actions: adopt modern authentication methods, enable centralized management of device configurations, and implement a secure program. An effective OT application security review should aim to identify and fix vulnerabilities, ensure the integrity of critical infrastructure, and manage compliance and risks. Vulnerabilities in OT systems can lead to service disruptions, data breaches, reputational harm, and compliance violations, making it crucial to address these issues proactively.
Leveraging AI for Cyber Defense
The threat landscape is rapidly evolving due to the rise of artificial intelligence (AI), which introduces both system and ecosystem threats. System threats often involve vulnerabilities in data processing systems, particularly those managed by third parties, where attackers can exploit weaknesses and insert malicious payloads. Users also tend to overrate the reliability of AI outputs, leading to further risks. Additionally, traditional cybersecurity vulnerabilities can affect underlying infrastructure, potentially exposing users to harmful content.
On a broader scale, ecosystem threats leverage AI for malicious purposes, such as impersonation and the creation of harmful content. These threats enable automated social engineering attacks like phishing, which can operate on a much larger scale, highlighting the need for enhanced defenses, including secure communication channels and AI tools for threat detection.
As the demand for cybersecurity professionals continues to rise, integrating AI into security operations becomes crucial. AI automates anomaly detection and vulnerability monitoring, streamlining security processes and enhancing overall effectiveness. For instance, Microsoft is developing innovative AI solutions to detect cyberattacks through endpoint stories, which compile data from various devices. This data, sourced from Microsoft Defender for Endpoint (MDE), improves the ability to identify and address threats effectively.
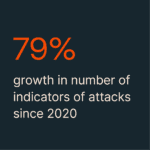
Furthermore, the number of indicators of attack reported by MDE has significantly increased, reflecting the growing complexity of cyber threats. Generative AI assists security teams in understanding these threats more contextually, allowing for more targeted remediation strategies and enhancing organizations’ overall security posture.
Conclusion: Harnessing AI for Cyber Defense
As cyber threats continue to evolve, so too must our defense strategies. Cybersecurity leaders need to take a proactive approach, focusing on threat-informed defense that integrates AI and automated systems to safeguard critical assets. Understanding attack paths, proactively monitoring data flows, and implementing robust defense mechanisms will be key to staying ahead of increasingly sophisticated cybercriminals.
AI’s role in cybersecurity will only grow in importance, providing organizations with the tools to better understand, detect, and defend against emerging threats. But to truly harness AI’s potential, organizations must ensure that their data environments are secure, prepared, and governed effectively.
To learn more about the findings in the Microsoft Digital Defense Report, download the report here.
As Microsoft’s US AI Partner of the Year, Neudesic is uniquely positioned to help you navigate the challenges of modernization, cybersecurity, and beyond. Click here to learn about Neudesic’s security solutions or Contact us today to get started.
Related Posts